bmzctf 刷题 elrond32
作者:互联网
bmzctf 刷题 elrond32
直接看mian函数

跟进sub_8048414函数
signed int __cdecl sub_8048414(_BYTE *a1, int a2)
{
signed int result; // eax
switch ( a2 )
{
case 0:
if ( *a1 == 105 )
goto LABEL_19;
result = 0;
break;
case 1:
if ( *a1 == 101 )
goto LABEL_19;
result = 0;
break;
case 3:
if ( *a1 == 110 )
goto LABEL_19;
result = 0;
break;
case 4:
if ( *a1 == 100 )
goto LABEL_19;
result = 0;
break;
case 5:
if ( *a1 == 97 )
goto LABEL_19;
result = 0;
break;
case 6:
if ( *a1 == 103 )
goto LABEL_19;
result = 0;
break;
case 7:
if ( *a1 == 115 )
goto LABEL_19;
result = 0;
break;
case 9:
if ( *a1 == 114 )
LABEL_19:
result = sub_8048414(a1 + 1, 7 * (a2 + 1) % 11);
else
result = 0;
break;
default:
result = 1;
break;
}
return result;
}
由前面的mian函数中的sub_8048414(a2[1], 0)可知,传入的a2为0,所以进入的是case 为0的环节,判断了一下指针a1后,进入了LABEL_19,在这里a2 = 7 * (a2 + 1) % 11,a2也就变成了7,然后再次进入sub_8048414,进入下一个switch轮回
这里可以写一段脚本算出来a2
a2 = 0
for i in range(9):
a2=7*(a2+1)%11
print (a2)
得到a2为7,1,3,6,5,9,4,2,10
因为switch里的选择只到了9,所以10不要,所以range应该为8轮
相应的就可以得到a1值,转为char型为isengard
这里可以把上一步和这一步合并一下
s='i'
a2 = 0
key = 'ie ndags r'
for i in range(8):
a2=7*(a2+1)%11
s += key[a2]
print (s)
可以得出程序需要的参数
运行一下
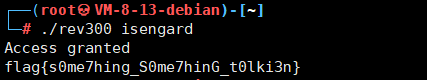
可以得到flag
根据伪代码求flag
但是也可以根据程序内的伪代码,算出flag
int __cdecl sub_8048538(int a1)
{
int v2[33]; // [esp+18h] [ebp-A0h]
int i; // [esp+9Ch] [ebp-1Ch]
qmemcpy(v2, &dword_8048760, sizeof(v2));
for ( i = 0; i <= 32; ++i )
putchar(v2[i] ^ *(a1 + i % 8));
return putchar(10);
}
其中dword_8048760地址处的值为
0x0F,0x1F,0x04,0x09,0x1C,0x12,0x42,0x09,0x0C,0x44,0x0D,0x07,0x09,0x06,0x2D,0x37,0x59,0x1E,0x00,0x59,0x0F,0x08,0x1C,0x23,0x36,0x07,0x55,0x02,0x0C,0x08,0x41,0x0A,0x14
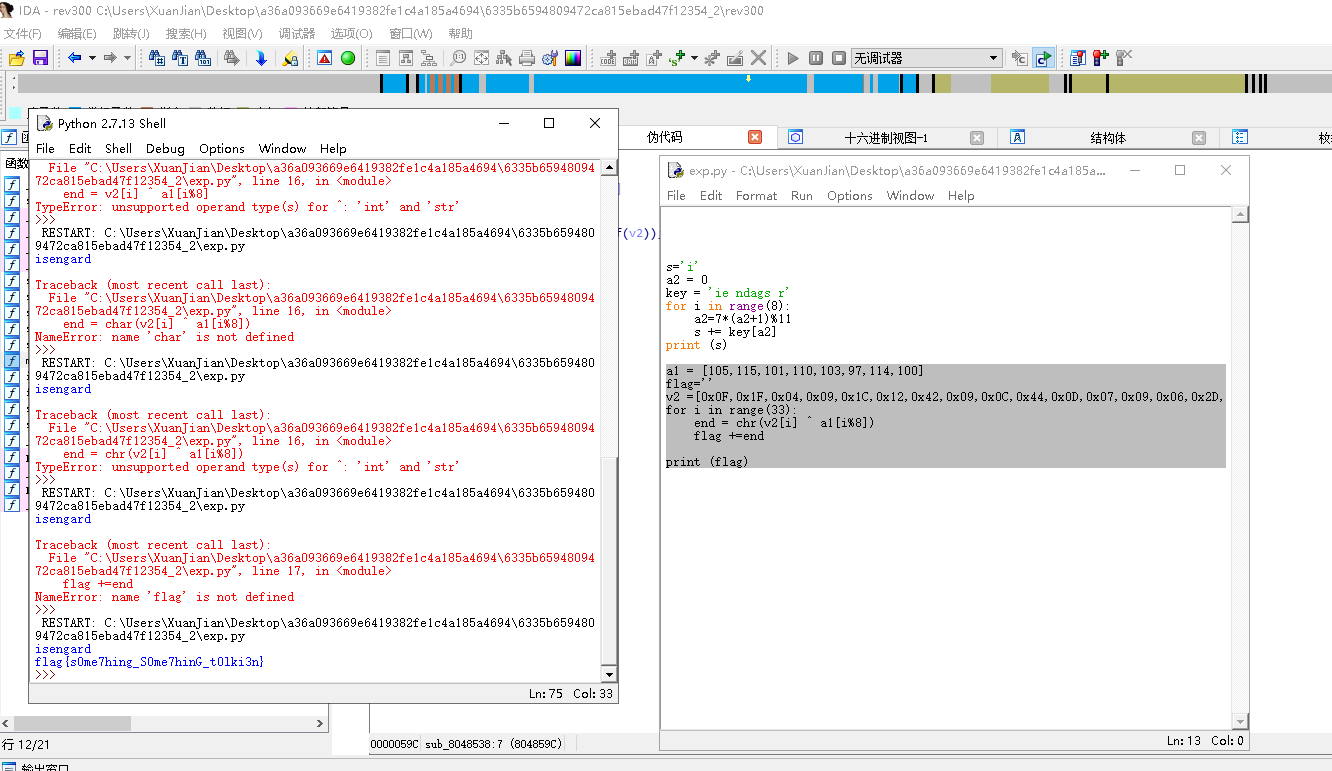
exp:
a1 = [105,115,101,110,103,97,114,100]
flag=''
v2 =[0x0F,0x1F,0x04,0x09,0x1C,0x12,0x42,0x09,0x0C,0x44,0x0D,0x07,0x09,0x06,0x2D,0x37,0x59,0x1E,0x00,0x59,0x0F,0x08,0x1C,0x23,0x36,0x07,0x55,0x02,0x0C,0x08,0x41,0x0A,0x14]
for i in range(33):
end = chr(v2[i] ^ a1[i%8])
flag +=end
print (flag)
在这里又把a1转换成了assic形式是为了方便异或运算
最后输出了flag
标签:case,break,bmzctf,elrond32,LABEL,a1,a2,result,刷题 来源: https://www.cnblogs.com/murkuo/p/15725804.html